Cybersecurity is serious business for any organization. In a compilation report, cybersecurity experts revealed these alarming statistics:
By 2017, there were more than 130 large-scale breaches per year in the U.S. Each year, that number grew by 27%.
- A malware attack costs an average of $2.4 million per company.
- From 2015 to 2017, the U.S. experienced 303 large-scale cyberattacks, the most of any nation within the period.
- 60% of malicious domains are associated with spam campaigns.
- 65% of companies have over 500 users who were never asked or reminded to change their passwords regularly.
- By 2019, the costs of ransomware damage will rise to $11.5 billion, with a business falling prey to a ransomware attack every 14 seconds.
Cybercriminals are always looking for new ways to bypass current cybersecurity measures. Unfortunately, security experts merely react to known attacks and are perennially playing catch-up to the bad guys.
So no matter how sophisticated cybersecurity has become, there are still must-have tools and services you need to keep your systems protected. Think of the following as your essential first line of defense; leave one out at your own expense.
#1 Firewall
Think of a firewall as the basic foundation of your cybersecurity arsenal. It’s a core security tool that blocks unauthorized access to your system from an untrusted external network, such as the internet. A firewall monitors your network’s internal traffic as well as screens all external attempts to connect to your network.
But as hackers become more sophisticated, they are able to devise new tricks to fool firewalls into allowing them access into your system. But no matter how malware evolves, a firewall is able to block a majority of attacks from less sophisticated or older kinds of malware. So a firewall is still a must-have.
#2 Antivirus software
Antivirus software alerts you for malware attacks, scans your email for malicious attachments and links, and quarantines or removes potential threats. Because malware is ever-changing, it’s important that your antivirus software is always up-to-date.
There is a wide range of antivirus software available in the market, so make sure you look for one that fits your business requirements.
#3 PKI services
Simply put, public key infrastructure (PKI) refers to security methods that allow two electronic identities to trust one another so they can exchange messages securely. They often involve identity authentication, data encryption, and digital signatures.
Others may refer to PKI as the “https” or the padlock they see on the left side of the browser address bar. However, PKI services also include:
- Multi-factor authentication — This ensures that only approved users and devices can access your network.
- Digital signatures — They allow for identity authentication and create a tamper-proof seal for documents to meet compliance requirements.
- Email encryption — This protects email from hacks and phishing attacks, and helps prevent data loss.
- Code protection — This protects codes from tampering and malware attacks, and verifies codes to assure end users that they are legitimate.
- Identification for IoT devices — As more and more devices become integrated with Internet of Things (IoT), it also becomes necessary to provide each IoT device its unique identity. This will provide further security and foster trust in the whole IoT ecosystem
#4 Managed detection services
Because criminals are always ahead of the game, cybersecurity has shifted from preventing attacks to identifying and eliminating attacks immediately, to minimize damage. Early detection and response is crucial, because it’s more difficult to fight off an attack already in full swing, and damage will be greater.
#5 Penetration test
Unlike a vulnerability scan, a penetration test involves security experts actually hacking into your system using the same techniques criminals use. This test reveals the full extent of your system’s vulnerabilities, and lets you see which data is exposed to hackers. Testers can now recommend the necessary improvements to ensure your network is better protected.
#6 Staff training
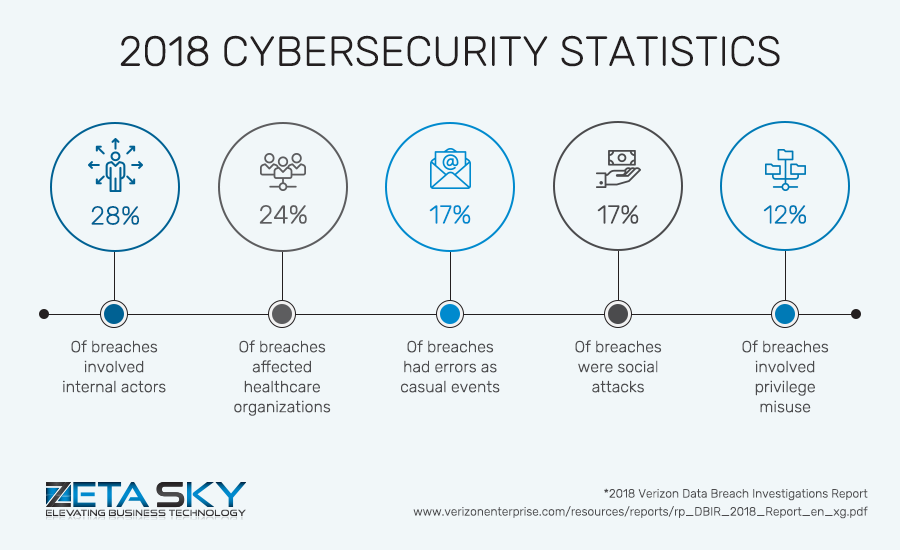
A 2018 data breach report stated that 28% of the breaches involved internal staff, 17% of breaches were due to errors, and another 17% due to social attacks. Outsiders may be beyond your control, but breaches from inside your organization can be prevented.
Train your staff on the current best practices for cybersecurity. Changes in cybersecurity happen often and swiftly, so make sure to conduct regular training sessions to keep everyone up-to-date. Things to focus on include:
- Best practices with passwords
- How to spot suspicious spam or scam mail
- How to guard against phishing attacks
- Social engineering tactics to avoid
An educated staff means everyone, not just your IT team, can contribute to keeping your systems safe.
Entrust your cybersecurity to Zeta Sky
Whether you have an internal IT team or not, you can’t go wrong partnering with a managed IT services provider (MSP) like Zeta Sky for your cybersecurity. Our experts will set up firewalls, intrusion prevention systems, and virtual private networks (VPNs). We’ll also monitor your system 24/7 with our specialized cybersecurity tools.
Aside from cybersecurity, Zeta Sky also offers cloud solutions, IT consulting, and more. We make sure your IT infrastructure is always optimized for your unique needs. Want to take your business sky high? Get in touch with us today.